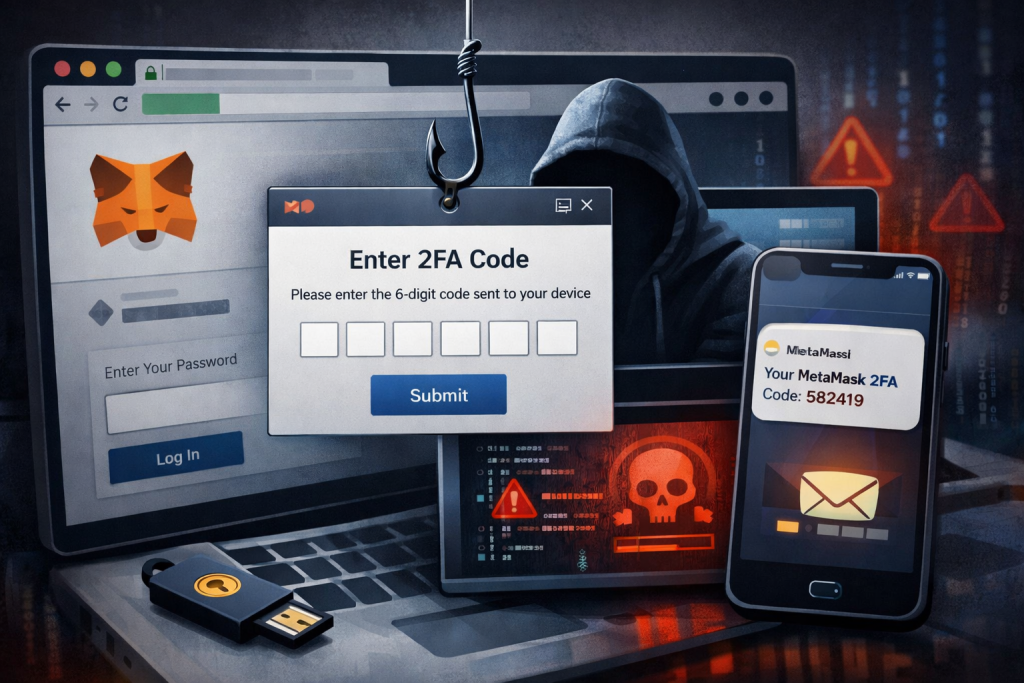
- Fake two-factor authentication phishing campaign emerges targeting MetaMask users.
- A sophisticated phishing scam targeting MetaMask users exploits fake 2FA checks.
- MetaMask phishing scam highlights rising social engineering risks in crypto security.
A new phishing campaign targeting MetaMask users is drawing attention to how quickly crypto scams are evolving.
The scheme uses a convincing two-factor authentication flow to trick users into handing over their wallet recovery phrases.
While overall crypto phishing losses fell sharply in 2025, the tactics behind these attacks are becoming more polished and harder to detect.
Security researchers say the campaign reflects a shift from crude spam messages to carefully designed impersonation, combining familiar branding, technical precision, and psychological pressure.
The result is a threat that looks routine on the surface but can lead to complete wallet takeover within minutes.
How the scam operates
The campaign was flagged by the chief security officer at SlowMist, who shared details on X.
The phishing emails are designed to look like official messages from MetaMask Support and claim that users must enable mandatory two-factor authentication.
They closely mirror the wallet provider’s branding, using the fox logo, colour palette, and layout that many users recognise.
A key part of the deception lies in the web domains used by attackers. In documented cases, the fake domain differed from the real one by just a single letter.
This small change makes it easy to miss, especially on mobile screens or when users are acting quickly.
Once the link is opened, victims are taken to a website that closely imitates MetaMask’s interface.
The fake 2FA process
On the phishing site, users are guided through what appears to be a standard security procedure.
Each step reinforces the idea that the process is legitimate and designed to protect the account.
At the final stage, the site asks users to enter their wallet seed phrase, presenting it as a required step to complete the two-factor authentication setup.
This is the decisive moment of the scam. A seed phrase, also known as a recovery or mnemonic phrase, functions as the master key to a wallet.
With it, an attacker can recreate the wallet on another device, transfer funds without approval, and sign transactions independently.
Passwords, two-factor authentication, and device confirmations become irrelevant once the phrase is compromised.
For this reason, wallet providers repeatedly warn users never to share recovery phrases under any circumstances.
The use of two-factor authentication as bait is deliberate.
2FA is widely associated with stronger security, which lowers suspicion.
When combined with urgency and professional presentation, it creates a false sense of safety.
Even experienced users can be caught off guard when a familiar security feature is turned into a tool for deception.
Early 2026 has already shown signs of renewed market activity, including meme coin rallies and growing retail participation.
As activity increases, attackers appear to be returning with more refined methods rather than higher volumes of low-quality scams.
The MetaMask phishing campaign suggests that future threats may rely less on scale and more on credibility.
For users of MetaMask and crypto wallets more broadly, the episode underlines the need for constant vigilance.
Security tools remain essential, but understanding how they can be misused is just as important as using them.
Crime,Phishing Attack#Fake #MetaMask #2FA #phishing #scam #polished #design #steal #wallet #seed #phrases1767603429